Minggu, 22 November 2009
VNC (Virtual Network Computing)
To install VNC it is very easy as well. It has its free edition.
I use VNC to control Optical DWDM Analyzer. I use JDSU. It is a kind of Optical spectrum analyzer that is specially designed for DWDM measurement. We an use USB memory stick to copy measurement result and process it in our desktop. But... it is very risky. Why? USB memory stick is potential to spead virus to our analyzer. So, i prefer to use VNC to display the result and capture the result by "print screen-ing" it.
About "print screen-ing" i will talk later. It uses a special software : SNAGIT.
Senin, 16 November 2009
Buy Gold Now for Your Future!
What rich man do if he get a million dollar? He will think the way to "reproduce" the money. He never think to spend his money except for his primary and secondary needs. What in his mind is investation!!!
I hope you get the point of my explanation above. Rich man thinks how to get more money from small amount of money. The answer is investation. The real rich man will invest his money into gold. He will buy gold coin or buy gold bullion. The one who buy gold coin is one who loves about art. For the one who don't care about art, he will purchase gold bullion. For him, the most important thing is the value of the gold. Art is not important. Either buy gold coin or buy bullion
is better than buying jewelery. Why? Although they are the same gold, you must pay more for production cost of jewelery. Another weakness of jewelery is selling price is lower than buying price. In the other word you will loss some money when you sell your jewelery.
So.. what are you waiting for. Buy gold coin , buy gold bullion now! For a better future!
Minggu, 28 Juni 2009
Online Course in ITU Academy
http://academy.itu.int/
To enroll the course you must obtain enrollment key. How to get enrollment key?
ITU usually invites particular enterprise or government institution to join the course. It gives enrollment key to the ones which are invited.
Senin, 15 Juni 2009
Direct TV
Consumers who purchased DirecTV equipment subscribe to various packages of DirecTV programming for which the subscriber pays a monthly fee. A subscriber also can order pay-per-view events and movies. DirecTV contracts with and pays program providers such as cable networks, motion picture distributors, sports leagues, event promoters, and other programming rights holders, for the right to distribute their programming to its subscribers. All programming distributed by DirecTV is delivered to its broadcast centers in Castle Rock, Colorado, and Los Angeles, California, where it is then digitized and compressed. The resulting signal is encrypted, or electronically scrambled, by DirecTV to prevent its unauthorized reception. DirecTV then transmits these signals to several satellites located in stationary orbit approximately 22,300 miles above the equator
Kamis, 04 Juni 2009
Blue Screen
Anybody knows what it is?
Let u s check the answer. I took this from wikipedia :
The Blue Screen of Death (also known as a stop error, BSoD, bluescreen, or Blue Screen of Doom) is a colloquialism used for the error screen displayed by some operating systems, most notably Microsoft Windows, after encountering a critical system error which can cause the system to shut down to prevent damage.
Bluescreens on NT-based Windows systems are usually caused by poorly-written device drivers or malfunctioning hardware. In the Win9x era, incompatible DLLs or bugs in the kernel of the operating system could also cause bluescreens. They can also be caused by physical faults such as faulty memory, power supplies, overheating of computer components, or hardware running beyond its specification limits. Bluescreens have been present in all Windows-based operating systems since Windows 3.1; earlier, OS/2 suffered the Black Screen of Death, and early builds of Windows Vista displayed the Red Screen of Death after a boot loader error.
Minggu, 10 Mei 2009
802.1x
"Port-based network access control makes use of the physical access characteristics of IEEE 802 LAN infrastructures in order to provide a means of authenticating and authorizing devices attached to a LAN port that has point-to-point connection characteristics, and of preventing access to that port in cases which the authentication and authorization fails. A port in this context is a single point of attachment to the LAN infrastructure." --- 802.1X-2001, page 1.

 Figure 802.1X: A wireless node must be authenticated before it can gain access to other LAN resources
Figure 802.1X: A wireless node must be authenticated before it can gain access to other LAN resourcesWhen a new wireless node (WN) requests access to a LAN resource, the access point (AP) asks for the WN's identity. No other traffic than EAP is allowed before the WN is authenticated (the "port" is closed).
The wireless node that requests authentication is often called Supplicant, although it is more correct to say that the wireless node contains a Supplicant. The Supplicant is responsible for responding to Authenticator data that will establish its credentials. The same goes for the access point; the Authenticator is not the access point. Rather, the access point contains an Authenticator. The Authenticator does not even need to be in the access point; it can be an external component.
EAP, which is the protocol used for authentication, was originally used for dial-up PPP. The identity was the username, and either PAP or CHAP authentication [RFC1994] was used to check the user's password. Since the identity is sent in clear (not encrypted), a malicious sniffer may learn the user's identity. "Identity hiding" is therefore used; the real identity is not sent before the encrypted TLS tunnel is up.
After the identity has been sent, the authentication process begins. The protocol used between the Supplicant and the Authenticator is EAP, or, more correctly, EAP encapsulation over LAN (EAPOL). The Authenticator re-encapsulates the EAP messages to RADIUS format, and passes them to the Authentication Server.
During authentication, the Authenticator just relays packets between the Supplicant and the Authentication Server. When the authentication process finishes, the Authentication Server sends a success message (or failure, if the authentication failed). The Authenticator then opens the "port" for the Supplicant.
After a successful authentication, the Supplicant is granted access to other LAN resources/Internet.
Sumber : http://tldp.org/HOWTO/html_single/8021X-HOWTO/
Jumat, 01 Mei 2009
MULTICAST TESTING USING SMART WINDOW
Finally i find a way to test Multicast service in IP network using Smart Window. :)
I found this way by my self!
Well... to understand how to use Smart Bits Application, such as Smart Window, we need to read the direction in help. Read it carefully, then you will find a light ho to operate Smart Bits for your IP device testing.
I want to tell you the detail about this. But not now. I will tell you later. Please be patient. I am planning to write a legal work instruction for multicast testing using Smart Window. I hope this document will be usefull for somebody else who will test multicast using Smart Window.
Kamis, 30 April 2009
Page Rank
Menyedihkan banget dong.
Masa page rank nya -1
T_T
Bukannya page rank terkecil itu 0 ??
Senin, 27 April 2009
Minggu, 26 April 2009
Coret2 tentang UU ITE
Jadi sekarang email, chat dan dokumen2 lain yang didapatkan dari dunia mayabisa menjadi evidence dalam bertransaksi.
Diundangkan 2008. Indonesia termasuk yang cepat mengaplikasikan UU ITE.
PP = presiden --> ngatur keseluruhan
PM = menteri --> ngatur internal departemen
UU ITE ini bisa menjadi anacaman dan peluang. Peluangnya tapi lebih banyak.
UU no 36 thn 99 --> telekomunikasi sudah diliberaralisasi. Kita bisa merambah ke broadcast dan perbankan.
Finnet = perkawinan antara telco dan perbankan
Telco skrg sudah menjadi ancaman bagi perbankan
Misal : e-voucher.
IPTV juga jadi ancaman bagi dunia broadcast. Kita akan mengeluarakan digital TV.
Undang-undang belum detail. Detailnya akan diturunkan di PP, PM, Kepdirjen, Perdirjen.
Untuk numbering ada di kepdirjen.
That's why UU ITE ini sangat strategis.
MATERI UNDANG-UNDANG ITE
Berlaku di indonesia dan di luar indonesia
Berlaku bagi semua orang
IE dan DE menjadi alat bukti yang sah!
Sertifikasi keandalan mirip2 sertifikat halal MUI atau BPOM (kalau di makanan)
Ada badan pengawas badan sertifikasi keandalan
Tanda tangan elektronik memiliki kekuatan hukum dan akibat hukum yang sah
Tanda tangan digital -> berbasis publik key infrastructure atau berbasis biometric
Sertifikasi digital dapat disimpan di smart card.
Penyelenggara sertifikasi elektronik harus berbadan hukum dan berdomisili di Indonesia, kalau asing harus terdaftar di Indonesia.
RE = registration authority
Seperti notaris yang akan mengecek alamat fisik.
Transaksi elektronik harus ada perjanjian elektroniknya. Berlaku untuk publik dan privat.
Transaksi elektronik memiliki syarat : subjektif dan objektif.
Subjektif : kesepakatan, dan kecakapan
Objektif : informasi valid, sebab yang halal.
Untuk lebih jelasnya, bisa baca dokumen UU ITE yang lebih lengkap. =D
Senin, 06 April 2009
Jitter For Beginner
What is jitter? Jitter is, as shown in Figure 1, is “the short-term variations of a signal with respect to its ideal position in time.”
Figure 1. Jitter in Clock Signals
This deviation in a clock’s output transition from its ideal position can negatively impact data transmission quality. In many cases, other signal deviations, like signal skew and coupled noise are combined and labeled as jitter.
Deviation (expressed in ±ps) can occur on either the leading edge or the trailing edge of a signal. Jitter may be induced and coupled onto a clock signal from several different sources and is not uniform over all frequencies.
Excessive jitter can increase the bit error rate (BER) of a communications signal by incorrectly transmitting a data bit stream. In digital systems, jitter can lead to a violation of timing margins, causing circuits to behave improperly. Accurate measurement of jitter is necessary for ensuring the reliability of a system.
Sources of Jitter
Common sources of jitter include:
- Internal circuitry of the phase-locked loop (PLL)
- Random thermal noise from a crystal
- Other resonating devices
- Random mechanical noise from crystal vibration
- Signal transmitters
- Traces and cables
- Connectors
- Receivers
Beyond these sources, termination dependency, cross talk, reflection, proximity effects, VCC sag, ground bounce, and electromagnetic interference (EMI) from nearby devices and equipment can also increase the amount of jitter in a device.
Reflection and cross-talk frequency-dependent effects may be amplified if an adjacent signal is synchronous and in phase. Aside from noise caused by power supplies and ground, changes in circuit impedance are responsible for most of the jitter in data transmission circuits.
Jitter Components
The two major components of jitter are random jitter, and deterministic jitter.
Random Jitter
The random component in jitter is due to the noise inherent in electrical circuits and typically exhibits a Gaussian distribution. Random jitter (RJ) is due to stochastic sources, such as substrate and power supply. Electrical noise interacts with the slew rate of signals to produce timing errors at the switching points.
RJ is additive as the sum of squares, and follows a bell curve. Since random jitter is not bounded, it is characterized by its standard deviation (rms) value.
Deterministic Jitter
Deterministic jitter (DJ) is data pattern dependant jitter, attributed to a unique source. Sources are generally related to imperfections in the behavior of a device or transmission media but may also be due to power supply noise, cross-talk, or signal modulation.
DJ is linearly additive and always has a specific source. This jitter component has a non-Gaussian probability density function and is always bounded in amplitude. DJ is characterized by its bounded, peak-to-peak, value.
Types of Jitter
There are many different types of jitter. Period jitter, cycle-to-cycle jitter and half-period jitter are described below.
Period Jitter
Period jitter is the change in a clock’s output transition (typically the rising edge) from its ideal position over consecutive clock edges. Period jitter is measured and expressed in time or frequency. Period jitter measurements are used to calculate timing margins in systems, such as tSU and tCO.
Cycle-to-Cycle Jitter
Cycle-to-cycle jitter is the difference in a clock’s period from one cycle to the next. Cycle-to-cycle jitter is the most difficult to measure usually requiring a timing interval analyzer.
As shown in Figure 2, J1 and J2 are the measured jitter values. The maximum value measured over multiple cycles is the maximum cycle-to-cycle jitter.
Figure 2. Cycle-to-Cycle Jitter
Half-Period Jitter
Half-period jitter is the measure of maximum change in a clock’s output transition from its ideal position during one-half period. Figure 3 illustrates half-period jitter.
Half-period jitter impacts DDR transfer applications by reducing capture margins.
Figure 3. Half-Period Jitter
Jitter Specifications
The performance of the PLL is measured using several parameters. Three of the common specifications used to characterize the PLL are jitter generation, tolerance, and transfer.
Jitter Generation
Jitter generation is the measure of the intrinsic jitter produced by the PLL and is measured at its output. Jitter generation is measured by applying a reference signal with no jitter to the input of the PLL, and measuring its output jitter. Jitter generation is usually specified as a peak-to-peak period jitter value.
Jitter Tolerance
Jitter tolerance is a measure of the ability of a PLL to operate properly (i.e., remain in lock in the presence of jitter of various magnitudes at different frequencies) when jitter is applied to its reference. Jitter tolerance is usually specified using an input jitter mask.
Jitter Transfer
Jitter transfer or jitter attenuation refers to the magnitude of jitter at the output of a device for a given amount of jitter at the input of the device. Input jitter is applied at various amplitudes and frequencies, and output jitter is measured with various bandwidth settings. Since intrinsic jitter is always present, jitter attenuation will appear to be lower for low frequency input jitter signals than for high frequency ones. Jitter transfer is typically specified using a bandwidth plot.
References
Lecroy. 2001. Jitter & Timing Analysis Training Presentation.
http://www.altera.com/support/devices/pll_clock/jitter/pll-jitter.html
Jumat, 27 Maret 2009
UdAH tERaGGREgASI
Alhamdulillah... semoga bisa bermanfaat untuk siapa pun yang membutuhkan informasi yang ada dalam blog ini...
Walaupun blognya cuman copas an dari site lain, semoga bisa memudahkan proses belajar bagi siapapun, terutama untuk saya sendiri :)
Ayo terus belajar..... Jangan pernah berhenti ;)
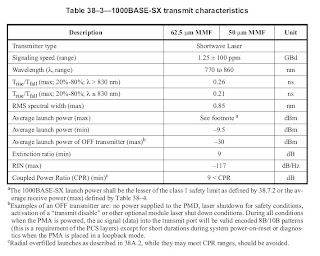
UNDERSTANDING LAUNCHED OPTICAL POWER WITHOUT INPUT TO TRANSMITTER
Launched optical power without input to transmitter is different from mean launched optical power.
The mean launched power at OLT and ONU/ONT is the average power of a pseudo-random data sequence coupled into the fibre by the transmitter. It is given as a range to allow for some cost optimization and to cover all allowances for operation under standard operating conditions, transmitter connector degradation, measurement tolerances, and ageing effects.
In operating state, the lower figure is the minimum power which shall be provided and the higher one is the power which shall never be exceeded.
NOTE - The measurement of the launched power at the ONU/ONT optical interface shall take into account the bursty nature of the upstream traffic transmitted by the ONU/ONT.
In the upstream direction, the ONU transmitter shall launch no power into the fibre in all slots which are not assigned to that ONU. The ONU shall also launch no power during the Guard time of slots that are assigned to it, with the exception of the last Tx Enable bits which may be used for laser pre bias, and the Tx Disable bits immediately following the assigned cell, during which the output falls to zero. The launched power level during laser pre-bias must be less than 0.1 of the one level.
www.mblast.com/files/companies/89960/Document/gpon_pmd_white_v01.doc
Optical Power Bidget Calculation
Solution
Optical power budget is term used to describe total amount of light energy amplitude available over a certain link path. The budget can be determined by subtracting the Receiver Sensitivity from the Optical Output Power. The optical budget serves as a useful estimation to determine if sufficient optical output power remains on the receiver side of an optical link. The optical power budget also refers to the allocation of available optical power (transmitted into a given fiber by a given source) among various loss-producing mechanisms.
The loss is caused by various factors. Typical losses are caused by fiber attenuation (per km), slice attenuation (per slice), and connector attenuation (per connector pair).
1. Power Budget = (Output / Launch Power) - (Receiver Sensitivity)
2. Worse case Optical Power Budget = (Min TX power) - (Max RX sensitivity) - (LED aging factor) - (insertion loss)
We'll use the following values to illustrate:
Min Tx Power = -9.5 dBm
Max Rx Sensitivity = -20 dBm
Estimated LED aging = 1 dB
Estimated Insertion loss = 1 dB
3. Therefore:
Optical Power Budget = (-9.5 dBm) - (-20 dBm)
Maximum Allowable Loss = 10.5 dB
4. Worst case OPB = Power Budget - Total Optical Power Loss =>
10.5 dB - 1dB (for LED aging) - 1dB (for insertion loss) - 1 dB (for per connector pair) - 2dB (safety factor) = 5 dB
5. Worst case distance = {Worst case OPB, in dB} / [Cable Loss, in dB/Km]
The Optical Power Budget is based on a theoretical calculation, and is for reference only. We still strongly recommend that you perform on-site testing to verify the result. On the data sheet, the supported fiber transmission distances are stated on each switch, with fiber port orSFP fiber modules. The customer can select the desired model without performing the power budget calculation.
http://www.moxa.com/support/faq/faq_detail.aspx?f_id=1239
Optical Power Bidget Calculation
Technical FAQs
| Question | How do I calculate the Optical Power Budget? |
| Question Type | Application |
| Updated | Feb 27,2008 |
| Hits | 797 |
| Products | SFP-1G Series, EDS-510A Series, EDS-726 Series, EDS-518A Series, EDS-516A Series, EDS-505A/508A Series, EDS-405A/408A Series, EDS-316 Series, EDS-309 Series, EDS-P308 Series, EDS-305-M12 Series, EDS-305/308 Series, EDS-205/208 Series, ED6008, EDS-405, EDS-50/505, OS5008, EDS-728 Series, PT-7 |
Solution
Optical power budget is term used to describe total amount of light energy amplitude available over a certain link path. The budget can be determined by subtracting the Receiver Sensitivity from the Optical Output Power. The optical budget serves as a useful estimation to determine if sufficient optical output power remains on the receiver side of an optical link. The optical power budget also refers to the allocation of available optical power (transmitted into a given fiber by a given source) among various loss-producing mechanisms.
The loss is caused by various factors. Typical losses are caused by fiber attenuation (per km), slice attenuation (per slice), and connector attenuation (per connector pair).
1. Power Budget = (Output / Launch Power) - (Receiver Sensitivity)
2. Worse case Optical Power Budget = (Min TX power) - (Max RX sensitivity) - (LED aging factor) - (insertion loss)
We'll use the following values to illustrate:
Min Tx Power = -9.5 dBm
Max Rx Sensitivity = -20 dBm
Estimated LED aging = 1 dB
Estimated Insertion loss = 1 dB
3. Therefore:
Optical Power Budget = (-9.5 dBm) - (-20 dBm)
Maximum Allowable Loss = 10.5 dB
4. Worst case OPB = Power Budget - Total Optical Power Loss =>
10.5 dB - 1dB (for LED aging) - 1dB (for insertion loss) - 1 dB (for per connector pair) - 2dB (safety factor) = 5 dB
5. Worst case distance = {Worst case OPB, in dB} / [Cable Loss, in dB/Km]
The Optical Power Budget is based on a theoretical calculation, and is for reference only. We still strongly recommend that you perform on-site testing to verify the result. On the data sheet, the supported fiber transmission distances are stated on each switch, with fiber port orSFP fiber modules. The customer can select the desired model without performing the power budget calculation.
Senin, 23 Maret 2009
Mengenal G.SHDSL
G.SHDL is the acronym of Giga Single-pair High bit rate Digital Subscriber Line (2)
G.SHDSL is a new international standard for single-pair, high-speed DSL, as defined in the ITU-T Standard G.991.2. Unlike asymmetric DSL, which was designed for residential applications in which more bandwidth is delivered downstream (to the house) than is available upstream (to the Internet), G.SHDSL is symmetrical - offering 2.3M bit/sec in both directions.
This makes G.SHDSL better-suited for business applications, which require higher-speed bandwidth in both directions.
G.SHDSL combines the positive aspects of existing copper-based, high-speed communications with the benefits of increased data rates, longer reach and less noise.
*DSL = Digital line subscriber(1) http://www.computerhope.com/jargon/g/gshdsl.htm
(2) http://www.acronymdb.com/acronym/G.SHDSL
Minggu, 22 Maret 2009
MLM dan SLM
MLM = Multi longitudinal mode
SLM = Singe longitudinal mode
Multi-mode and Single-mode optical fiber
Figure 2. Single-Mode and Multimode Fibers
Multi-mode optical fiber (multimode fiber or MM fiber or fibre) is a type of optical fiber mostly used for communication over shorter distances, such as within a building or on a campus. Typical multimode links have data rates of 10 Mbit/s to 10 Gbit/s over link lengths of up to 600 meters—more than sufficient for the majority of premises applications.
Multimode fiber was the first type of fiber to be commercialized. It has a much larger core than single-mode fiber, allowing hundreds of modes of light to propagate through the fiber simultaneously. Additionally, the larger core diameter of multimode fiber facilitates the use of lower-cost optical transmitters (such as light emitting diodes [LEDs] or vertical cavity surface emitting lasers [VCSELs]) and connectors.
Single-mode fiber, on the other hand, has a much smaller core that allows only one mode of light at a time to propagate through the core. While it might appear that multimode fibers have higher capacity, in fact the opposite is true. Singlemode fibers are designed to maintain spatial and spectral integrity of each optical signal over longer distances, allowing more information to be transmitted.
Its tremendous information-carrying capacity and low intrinsic loss have made single-mode fiber the ideal transmission medium for a multitude of applications. Single-mode fiber is typically used for longer-distance and higher-bandwidth applications (see Figure 3). Multimode fiber is used primarily in systems with short transmission distances (under 2 km), such as premises communications, private data networks, and parallel optic applications.
While fiber optic cable itself has become cheaper over time - a equivalent length of copper cable cost less per foot but not in capacity. Fiber optic cable connectors and the equipment needed to install them are still more expensive than their copper counterparts.
Single Mode cable is a single stand (most applications use 2 fibers) of glass fiber with a diameter of 8.3 to 10 microns that has one mode of transmission. Single Mode Fiber with a relatively narrow diameter, through which only one mode will propagate typically 1310 or 1550nm. Carries higher bandwidth than multimode fiber, but requires a light source with a narrow spectral width. Synonyms mono-mode optical fiber, single-mode fiber, single-mode optical waveguide, uni-mode fiber.
Single Modem fiber is used in many applications where data is sent at multi-frequency (WDM Wave-Division-Multiplexing) so only one cable is needed - (single-mode on one single fiber)
Single-mode fiber gives you a higher transmission rate and up to 50 times more distance than multimode, but it also costs more. Single-mode fiber has a much smaller core than multimode. The small core and single light-wave virtually eliminate any distortion that could result from overlapping light pulses, providing the least signal attenuation and the highest transmission speeds of any fiber cable type.
Single-mode optical fiber is an optical fiber in which only the lowest order bound mode can propagate at the wavelength of interest typically 1300 to 1320nm.
jump to single mode fiber page
Multi-Mode cable has a little bit bigger diameter, with a common diameters in the 50-to-100 micron range for the light carry component (in the US the most common size is 62.5um). Most applications in which Multi-mode fiber is used, 2 fibers are used (WDM is not normally used on multi-mode fiber). POF is a newer plastic-based cable which promises performance similar to glass cable on very short runs, but at a lower cost.
Multimode fiber gives you high bandwidth at high speeds (10 to 100MBS - Gigabit to 275m to 2km) over medium distances. Light waves are dispersed into numerous paths, or modes, as they travel through the cable's core typically 850 or 1300nm. Typical multimode fiber core diameters are 50, 62.5, and 100 micrometers. However, in long cable runs (greater than 3000 feet [914.4 meters), multiple paths of light can cause signal distortion at the receiving end, resulting in an unclear and incomplete data transmission so designers now call for single mode fiber in new applications using Gigabit and beyond.
The use of fiber-optics was generally not available until 1970 when Corning Glass Works was able to produce a fiber with a loss of 20 dB/km. It was recognized that optical fiber would be feasible for telecommunication transmission only if glass could be developed so pure that attenuation would be 20dB/km or less. That is, 1% of the light would remain after traveling 1 km. Today's optical fiber attenuation ranges from 0.5dB/km to 1000dB/km depending on the optical fiber used. Attenuation limits are based on intended application.
sumber :
http://www.iec.org/online/tutorials/fiber_optic/topic02.asp
http://en.wikipedia.org/wiki/Multi-mode_fiber
http://www.arcelect.com/fibercable.htm
IP Multicast to MAC Address Mapping
Map Multicast MAC address to IP Multicast Addresses
In the course of reading through the BSCI authorize self-study guide, I’ve come across a multicast example where the author talks about the concepts behind the multicast IP to MAC address mapping.
- In order to achieve the translation between a Layer 3 IP multicast address and Layer 2 multicast MAC address, the low-order 23 bits of the IP address (Layer 3) is mapped into the low-order 23 bits of the MAC address (Layer 2).
- The high order 4 bits of the Layer 3 IP address is fixed to 1110 to indicate the Class D address space between 224.0.0.0 through 239.255.255.255
- Ethernet MAC addresses start with 01:00:5E, allowing for a range from 01:00:5E:00:00:00 through 01:00:5E:7F:FF:FF.
- With 32 total bits present in an IP address and 4 high order bits of it set at 1110, we are left with 28 bits of unique IP addresses we can use (32 - 4 = 28).
- But remember, 23 low-order bits out of the 28 available bits are mapped to the MAC address, giving us 5 remaining bits of overlap.
- With the 5 bits of extra overlap, there are 32 (25 = 32) IP multicast address that map to one MAC multicast address.
The problem is, the book does not explain or show how it solved the mapping. So I went about researching how it was done. If you happened to be studying for BSCI, I am referring to the section of the BSCI: Authorized Self-Study Guide, by Teare and Paquet, that starts on page 598 - 600.
The following is an example of how we arrive with those 32 IP addresses that map to a single MAC address:
For reference, use the following conversion chart for converting hex to binary and vice versa
Let’s start by using the example MAC address given in the book :
01:00:5e:0a:00:01
- Convert the hexadecimal MAC address 01:00:5e:0a:00:01 to binary
- Isolate the 23 low-order binary bits from the converted MAC address:
- 0000 0001 : 0000 0000 : 0101 1110 : 0000 1010 : 0000 0000 : 0000 0001
- Take the low order 23 bits from step 2 and plug it into the low-order 23 bits of the IP address (do this in binary):
- 1110 xxxx : x000 1010 : 0000 0000 : 0000 0000
- 1110 - First 4 high-order bits of the IP address for the multicast address space (224.x.x.x).
- xxxx x - 5 remaining bits after the 23bits of the IP address is mapped to the MAC address plus the 4 high order bits 1110. This is equal to 32 total IP addresses.
- 1110 xxxx : x000 1010 : 0000 0000 : 0000 0000
- Convert the binary equivalent of the IP addresses to decimal, replacing the x variables with all the values to get all 32 possible IP addresses:
- 1110 0000 : 0000 1010 : 0000 0000 : 0000 0001 = 224.10.0.1
- 1110 0001 : 0000 1010 : 0000 0000 : 0000 0001 = 225.10.0.1
- 1110 0010 : 0000 1010 : 0000 0000 : 0000 0001 = 226.10.0.1
- 1110 0011 : 0000 1010 : 0000 0000 : 0000 0001 = 227.10.0.1
- 1110 0100 : 0000 1010 : 0000 0000 : 0000 0001 = 228.10.0.1
- 1110 0101 : 0000 1010 : 0000 0000 : 0000 0001 = 229.10.0.1
- 1110 0110 : 0000 1010 : 0000 0000 : 0000 0001 = 230.10.0.1
- 1110 0111 : 0000 1010 : 0000 0000 : 0000 0001 = 231.10.0.1
- 1110 1000 : 0000 1010 : 0000 0000 : 0000 0001 = 232.10.0.1
- 1110 1001 : 0000 1010 : 0000 0000 : 0000 0001 = 233.10.0.1
- 1110 1010 : 0000 1010 : 0000 0000 : 0000 0001 = 234.10.0.1
- 1110 1011 : 0000 1010 : 0000 0000 : 0000 0001 = 235.10.0.1
- 1110 1100 : 0000 1010 : 0000 0000 : 0000 0001 = 236.10.0.1
- 1110 1101 : 0000 1010 : 0000 0000 : 0000 0001 = 237.10.0.1
- 1110 1110 : 0000 1010 : 0000 0000 : 0000 0001 = 238.10.0.1
- 1110 1111 : 0000 1010 : 0000 0000 : 0000 0001 = 239.10.0.1
- 1110 0000 : 1000 1010 : 0000 0000 : 0000 0001 = 224.10.0.1
- 1110 0001 : 1000 1010 : 0000 0000 : 0000 0001 = 225.138.0.1
- 1110 0010 : 1000 1010 : 0000 0000 : 0000 0001 = 226.138.0.1
- 1110 0011 : 1000 1010 : 0000 0000 : 0000 0001 = 227.138.0.1
- 1110 0100 : 1000 1010 : 0000 0000 : 0000 0001 = 228.138.0.1
- 1110 0101 : 1000 1010 : 0000 0000 : 0000 0001 = 229.138.0.1
- 1110 0110 : 1000 1010 : 0000 0000 : 0000 0001 = 230.138.0.1
- 1110 0111 : 1000 1010 : 0000 0000 : 0000 0001 = 231.138.0.1
- 1110 1000 : 1000 1010 : 0000 0000 : 0000 0001 = 232.138.0.1
- 1110 1001 : 1000 1010 : 0000 0000 : 0000 0001 = 233.138.0.1
- 1110 1010 : 1000 1010 : 0000 0000 : 0000 0001 = 234.138.0.1
- 1110 1011 : 1000 1010 : 0000 0000 : 0000 0001 = 235.138.0.1
- 1110 1100 : 1000 1010 : 0000 0000 : 0000 0001 = 236.138.0.1
- 1110 1101 : 1000 1010 : 0000 0000 : 0000 0001 = 237.138.0.1
- 1110 1110 : 1000 1010 : 0000 0000 : 0000 0001 = 238.138.0.1
- 1110 1111 : 1000 1010 : 0000 0000 : 0000 0001 = 239.138.0.1
- All the 32 IP addresses on step 4 map to MAC address 01:00:5e:0a:00:01
Convert IP Multicast Address to Multicast MAC Address
Conversely, a multicast IP address can be converted to its equivalent MAC address. Once you’ve figured out how to convert from Layer 2 MAC to Layer 3 IP, doing the reverse is easy.
To start, we can pick any address from the 32 IP addresses we converted above. Let’s pick a random one like 227.138.0.1
- First convert the address 227.138.0.1 to binary:
- 11100011 : 10001010 : 00000000 : 00000001
- We’re only concerned with the red colored portion which represents the low-order 23bits of the IP address.
- Notice that we are dropping the high order bit of the second octet.
- Convert those 23 bits to hexadecimal:
- 0A:00:01
- We already know that the first 3-bytes (24 bits) of the MAC address is 01:00:5E. This was established earlier in the article. Simply append the result on step 2 to the first 3-bytes and you have your MAC address:
- 01:00:5E:0A:00:01
- *You can pick any of the 32 Ip addresses we have on the list above and you will always get 01:00:5E:0A:00:01 as your MAC address following the steps just mentioned.
To summarize:
- 1st octet - Notice that the first octet is left alone.
- 2nd octet - You only need to convert the last 7 bits to hex. The second octet in decimal is 138. But if you drop the highest order bit, it becomes a decimal 10 or hex 0A.
- 3rd octet - Convert it directly to hex.
- 4th octet - Convert it directly to hex.
Rabu, 18 Maret 2009
Learning Spot
Blog Design by Gisele Jaquenod